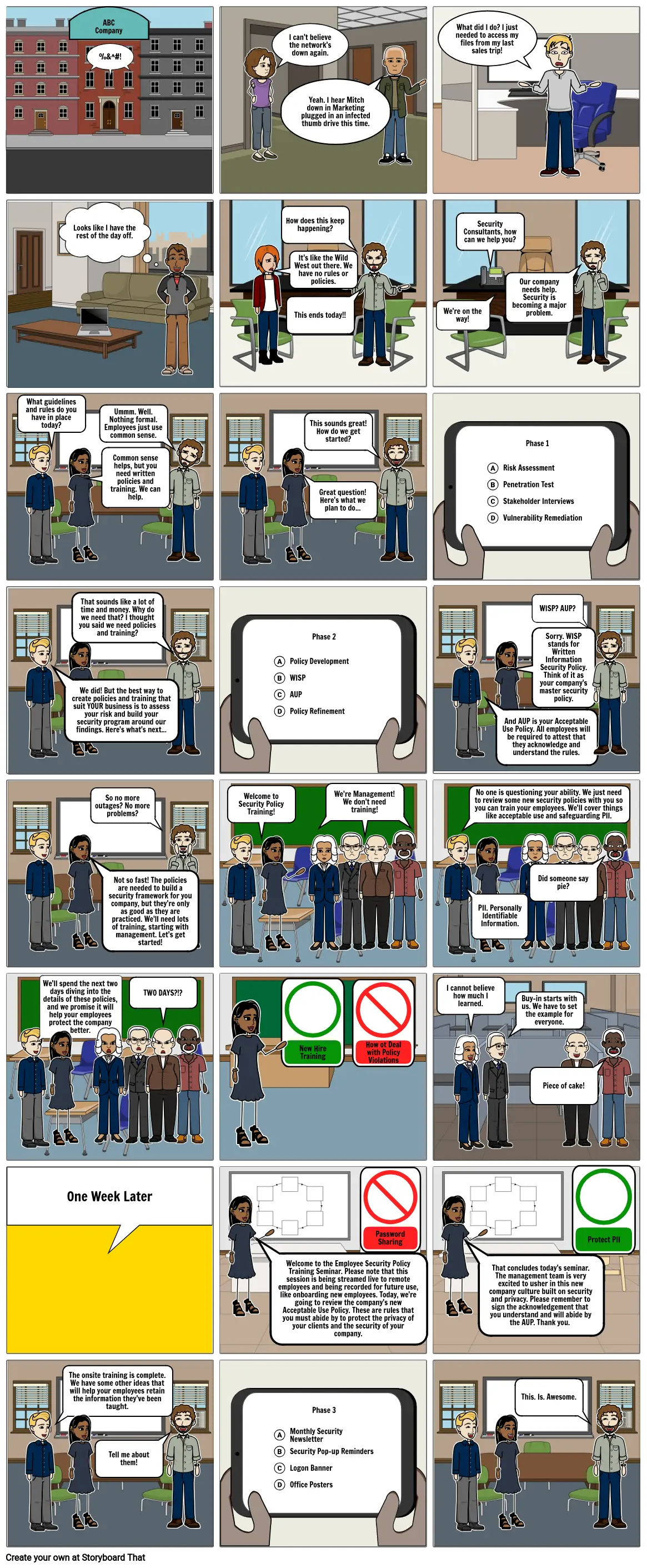
ABC Company
Storyboard-Text
- ABCCompany
- %&^#!
- I can't believe the network's down again.
- Yeah. I hear Mitch down in Marketing plugged in an infected thumb drive this time.
- What did I do? I just needed to access my files from my last sales trip!
- Looks like I have the rest of the day off.
- It's like the Wild West out there. We have no rules or policies.
- How does this keep happening?
- This ends today!!
- We're on the way!
- Security Consultants, how can we help you?
- Our company needs help. Security is becoming a major problem.
- What guidelines and rules do you have in place today?
- Common sense helps, but you need written policies and training. We can help.
- Ummm. Well. Nothing formal. Employees just use common sense.
- Great question! Here's what we plan to do...
- This sounds great! How do we get started?
- Phase 1 Risk Assessment Penetration Test Stakeholder Interviews Vulnerability Remediation
- We did! But the best way to create policies and training that suit YOUR business is to assess your risk and build your security program around our findings. Here's what's next...
- That sounds like a lot of time and money. Why do we need that? I thought you said we need policies and training?
- Phase 2 Policy Development WISP AUP Policy Refinement
- And AUP is your Acceptable Use Policy. All employees will be required to attest that they acknowledge and understand the rules.
- Sorry. WISP stands for Written Information Security Policy. Think of it as your company's master security policy.
- WISP? AUP?
- Not so fast! The policies are needed to build a security framework for you company, but they're only as good as they are practiced. We'll need lots of training, starting with management. Let's get started!
- So no more outages? No more problems?
- Welcome to Security Policy Training!
- We're Management! We don't need training!
- No one is questioning your ability. We just need to review some new security policies with you so you can train your employees. We'll cover things like acceptable use and safeguarding PII.
- PII. Personally Identifiable Information.
- Did someone say pie?
- We'll spend the next two days diving into the details of these policies, and we promise it will help your employees protect the company better.
- TWO DAYS?!?
- New Hire Training
- How ot Deal with Policy Violations
- I cannot believe how much I learned.
- Buy-in starts with us. We have to set the example for everyone.
- Piece of cake!
- One Week Later
- Welcome to the Employee Security Policy Training Seminar. Please note that this session is being streamed live to remote employees and being recorded for future use, like onboarding new employees. Today, we're going to review the company's new Acceptable Use Policy. These are rules that you must abide by to protect the privacy of your clients and the security of your company.
- Password Sharing
- That concludes today's seminar. The management team is very excited to usher in this new company culture built on security and privacy. Please remember to sign the acknowledgement that you understand and will abide by the AUP. Thank you.
- Protect PII
- The onsite training is complete. We have some other ideas that will help your employees retain the information they've been taught.
- Tell me about them!
- Phase 3 Monthly Security Newsletter Security Pop-up Reminders Logon Banner Office Posters
- This. Is. Awesome.
Über 30 Millionen erstellte Storyboards

